Table of Contents
1. IN-PROGRESS Understanding Birar
1.1. Introduction about this guide
Welcome to this dive into Briar. I never seen an app as secure and private as Briar. So I started to look at what exactly was behind it and started to get really interested.
It’s also a great opportunity to talk about various interesting things such as symmetric and asymmetric cryptography, forward secrecy, key exchanges, TOR and TOR Hidden Services, and of course Briar and its protocols (Bramble).
This page is work in progress so I guess I still need to remove some technical jargon from it. You can find all my sources at the end of the page.
1.2. What even is Briar?
Briar is a messaging app designed for activists, journalists, and anyone else who needs a safe, easy and robust way to communicate. Unlike traditional messaging apps, Briar doesn’t rely on a central server - messages are synchronized directly between the users’ devices. If the internet’s down, Briar can sync via Bluetooth or Wi-Fi, keeping the information flowing in a crisis. If the internet’s up, Briar can sync via the Tor network, protecting users and their relationships from surveillance.
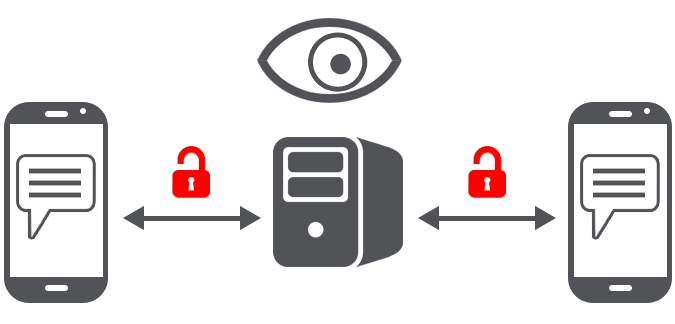
Figure 1: Example of unsecure traditional messaging
This is an example of insecure traditional messaging which leaks data and metadata about users which can be sold and/or collected by governments for surveillance.
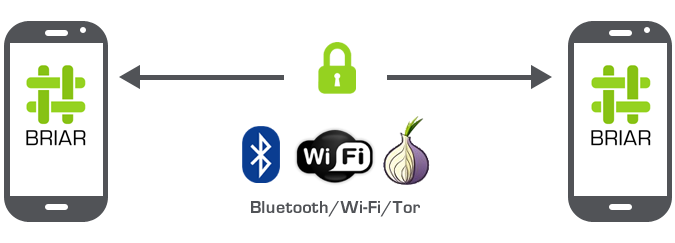
Figure 2: Example of how Briar works
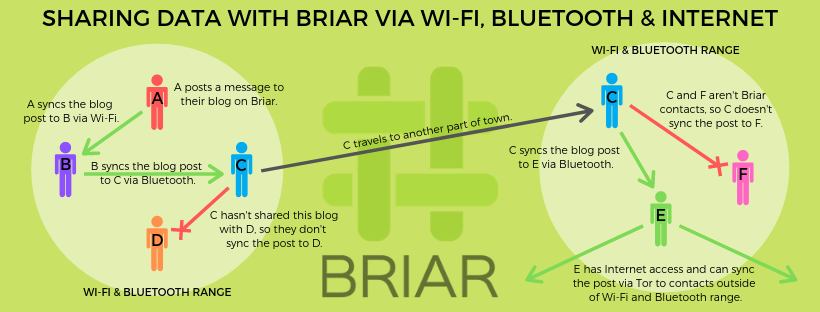
Figure 3: another more detailed example
While this is an example of how Briar works, with no central server, therefore no way to collect or sell data. This is obviously a very gross oversimplification, so we’re gonna get into much more details now.
1.2.1. How secure is Briar
Briar is protected against:
- Metadata surveillance. There are no central server and all traffic are either local or through TOR hidden services network.
- Content surveillance. All communication between devices is encrypted end-to-end, protecting the content from eavesdropping or tampering.
- Content filtering. Briar’s end-to-end encryption prevents keyword filtering, and because of its decentralized design there are no servers to block.
- Takedown orders. Every user who subscribes to a forum keeps a copy of its content, so there’s no single point where a post can be deleted.
- Denial of service attacks. Briar’s forums have no central server to attack, and every subscriber has access to the content even if they’re offline. Internet blackouts. Briar can operate over Bluetooth and Wi-Fi to keep information flowing during blackouts.
With a limited protection against:
- Spywares on the phone. The app prevents being drawn over by other apps, screen recording or screenshooting.
- Stealing and accessing the data. The app can be very easily signed out and data deleted. Meaning that if you are signed out, a stealer or hacker can’t decrypt your messages. And if everything is removed they can’t even know you ever used the app.
1.2.2. Briar comparison to other protocols
Here’s how Briar compares to other protocols in terms of protection, cryptographic abilities
| Properties | Discord | Signal | Matrix/Element | Conversations (XMPP over TOR and with OMEMO) | Briar |
|---|---|---|---|---|---|
| Network type | Centralized | Centralized | Federated | Federated | Peer to Peer |
| E2E encrypted | ❌ | ✅ | ✅ | ✅ | ✅ |
| Peer-to-Peer | ❌ | ❌ | ❌ | ❌ | ✅ |
| Ability to work offline (bluetooth, LAN, etc) | ❌ | ❌ | ❌ | ❌ | ✅ |
| TOR Hidden Services | ❌ | ❌ | ❌ | ✅ | ✅ |
| Protection against theft (while signed out) or screen recording | ❌ | ❌ | ❌ | ❌ | ✅ |
| Protection against metadata surveillance | ❌ | ❌ | ❌ | ✅ | ✅ |
| Protection against content surveillance | ❌ | ✅ | ✅ | ✅ | ✅ |
| Protection against takedown and DDoS attacks | ❌ | ❌ | ➕ | ➕ | ✅ |
| Anonymity | ❌ | ❌ | ❌ | ✅ | ✅ |
| Unlinkability | ❌ | ❌ | ❌ | ✅ | ✅ |
| Unobservability | ❌ | ❌ | ❌ | ✅ | ✅ |
| Operating over several modes of transport | ❌ | ❌ | ❌ | ❌ | ✅ |
| Support for images | ✅ | ✅ | ✅ | ✅ | ❌ |
| Support for calls | ✅ | ✅ | ✅ | ✅ | ❌ |
| Support for chat history (receiving messages while offline) | ✅ | ✅ | ✅ | ✅ | ❌ |
1.3. Some basics
Before diving into Briar’s protocols, we first need to understand some basics of networking and cryptography. What we’ll learn (in a very simplified manner) here is what is symmetric and asymmetric cryptography, what is diffie-hellman and how TOR hidden services work.
1.3.1. Symmetric encryption, asymmetric encryption and diffie-hellman
To be able to understand what follows we need to understand the difference betweeen symmetric and asymmetric cryptography and also understand what is called the Diffie-Hellman Key Exchange.
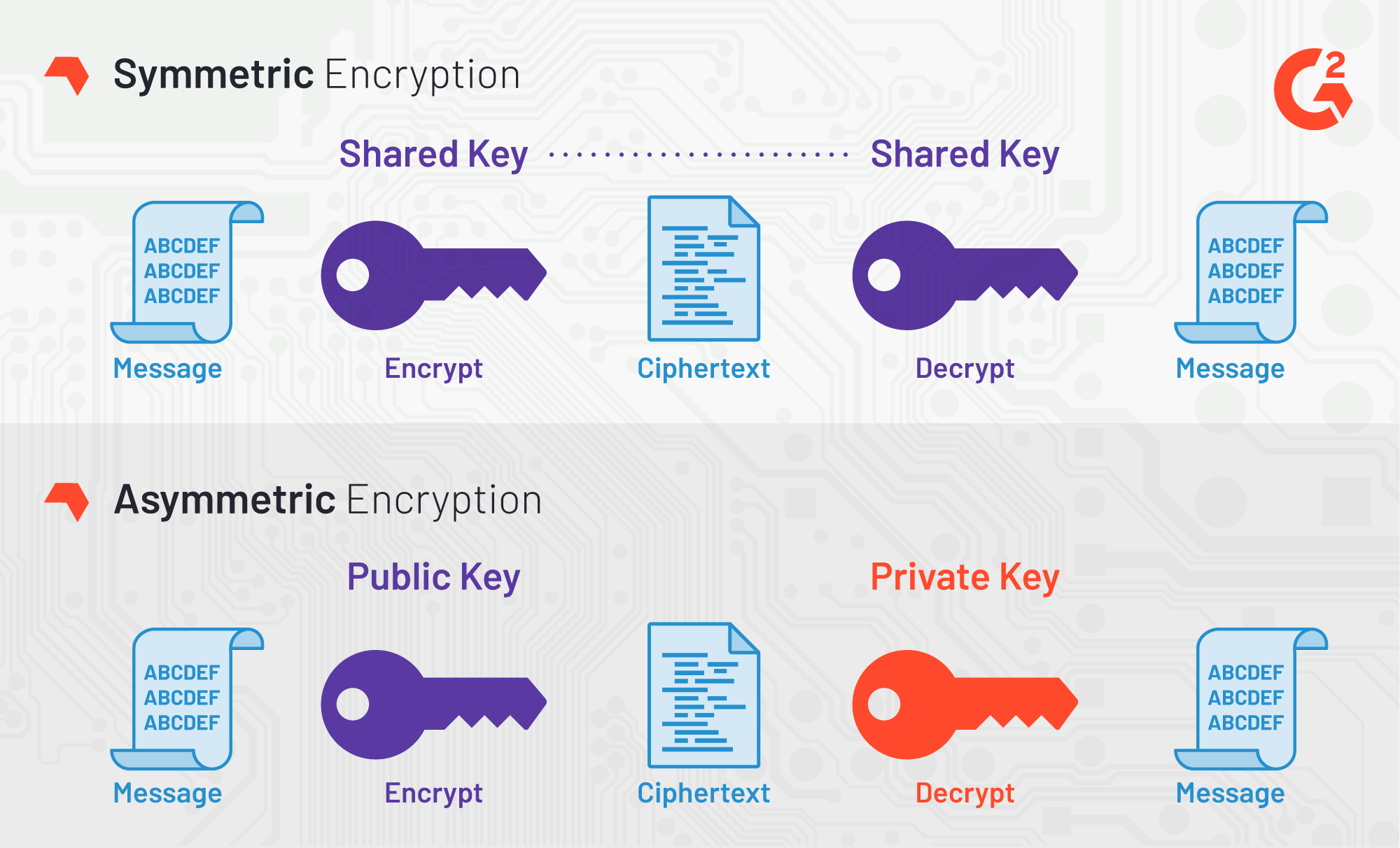
For the sake of time and your sanity (and mine) we’re gonna limit the difference between symmetric and asymmetric cryptography to this for the moment:
- Symmetric cryptography has one key that can encrypt and decrypt messages. It been used for hundreds of years and is very quick.
- Asymmetric cryptography has two keys, one for encrypting and one for decrypting. It’s much more recent but also much more resource-intensive and slow.
But we can get the best of both worlds by using the “Diffie-Hellman” algorithm. Which starts with asymmetric cryptography to exchange keys and generate a shared secret that can be used to continue in the less resource intensive symmetric cryptography.

The Diffie-Hellman algorithm consists of mixing the public key of the other person with your private key (the other person does the same). Which results at the end with the same shared secret.
1.3.2. How TOR (and TOR hidden services) works
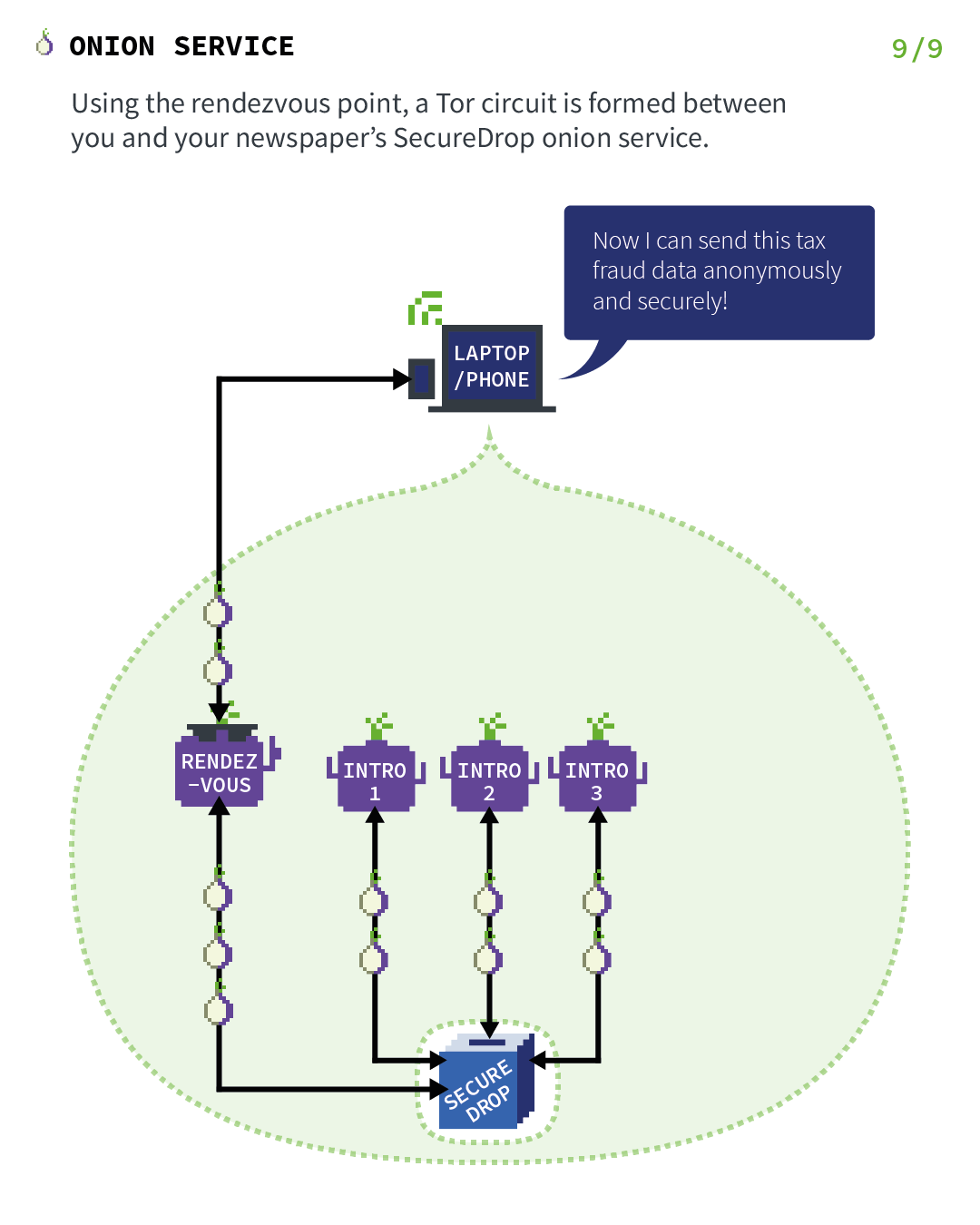
TOR and hidden services is an important point in Briar when Briar operates a remote connection.
So let’s explain the basics of TOR Hidden Services. Let’s start with a server and a client, but just remember that in the case of Briar, both people are servers and clients at the same time. Those images have been found on the official Tor Project’s website and will explain it much better than I ever will.
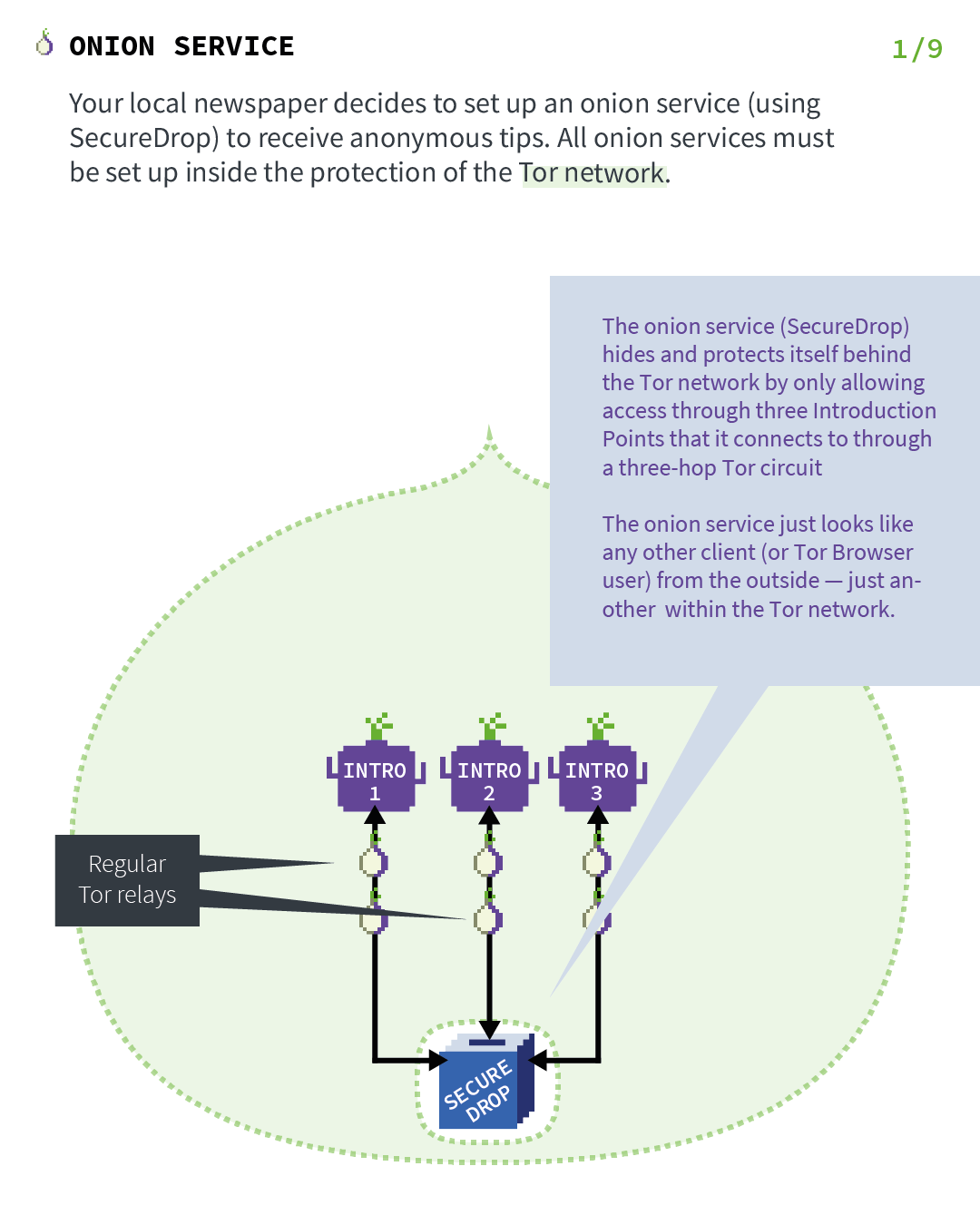
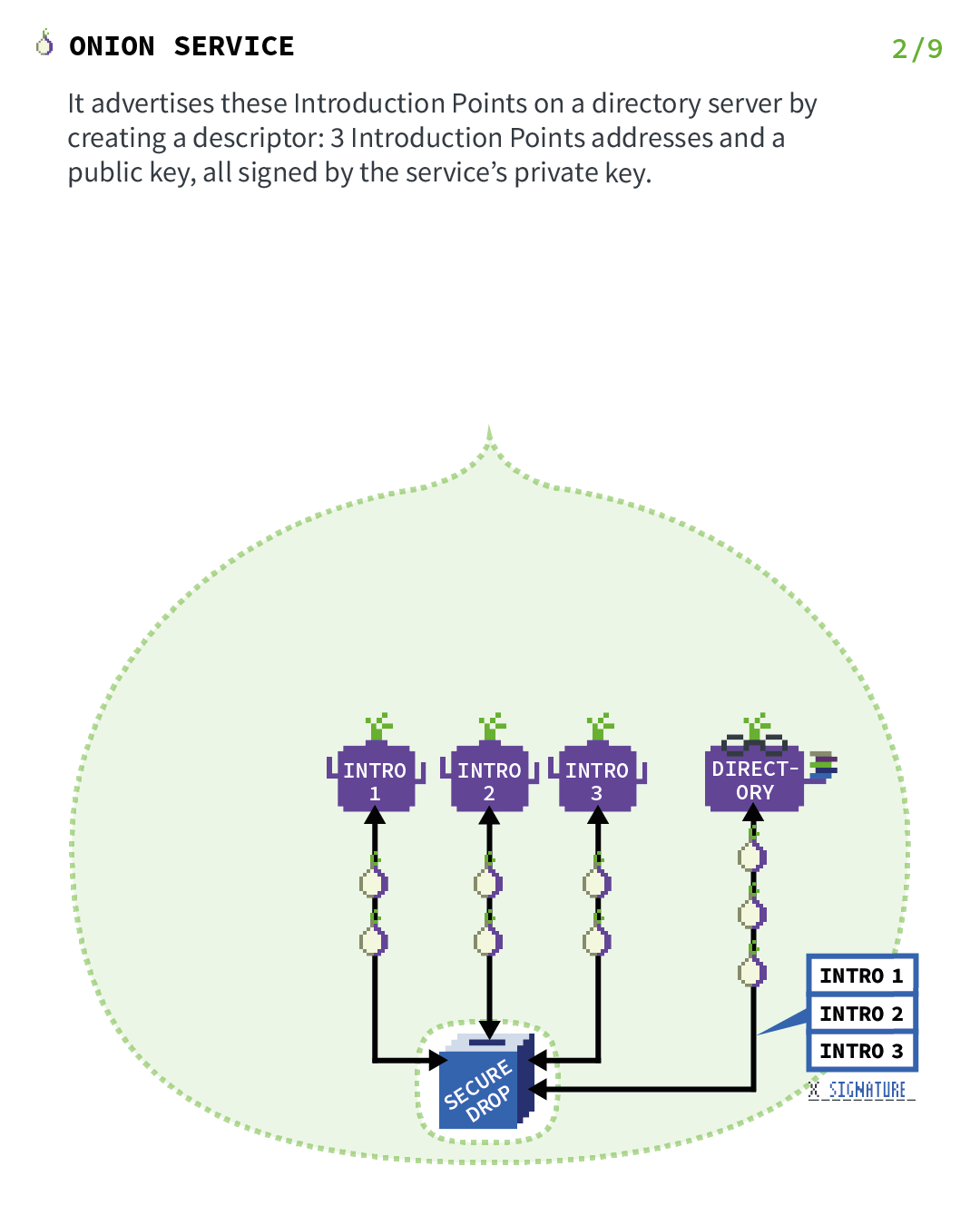
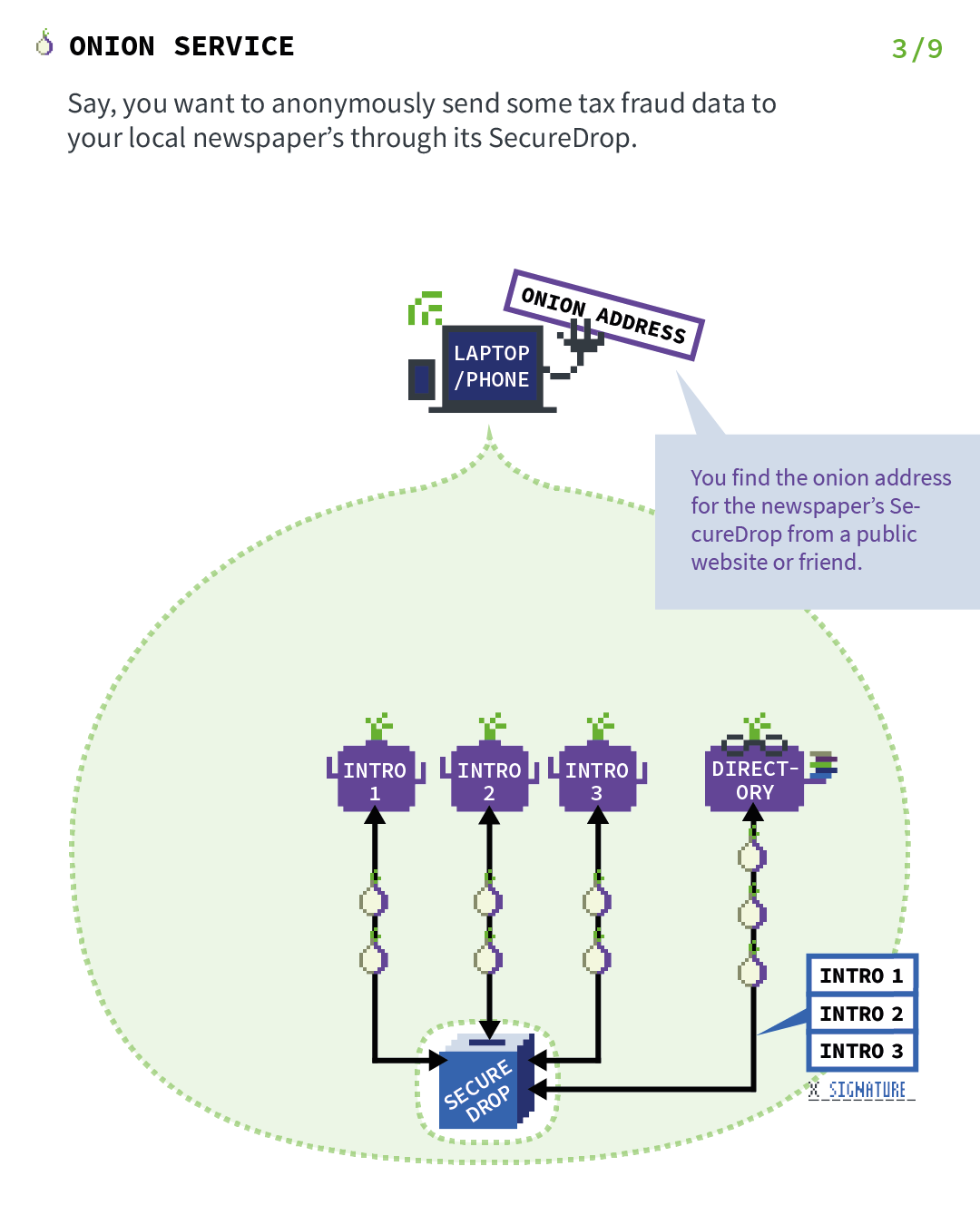
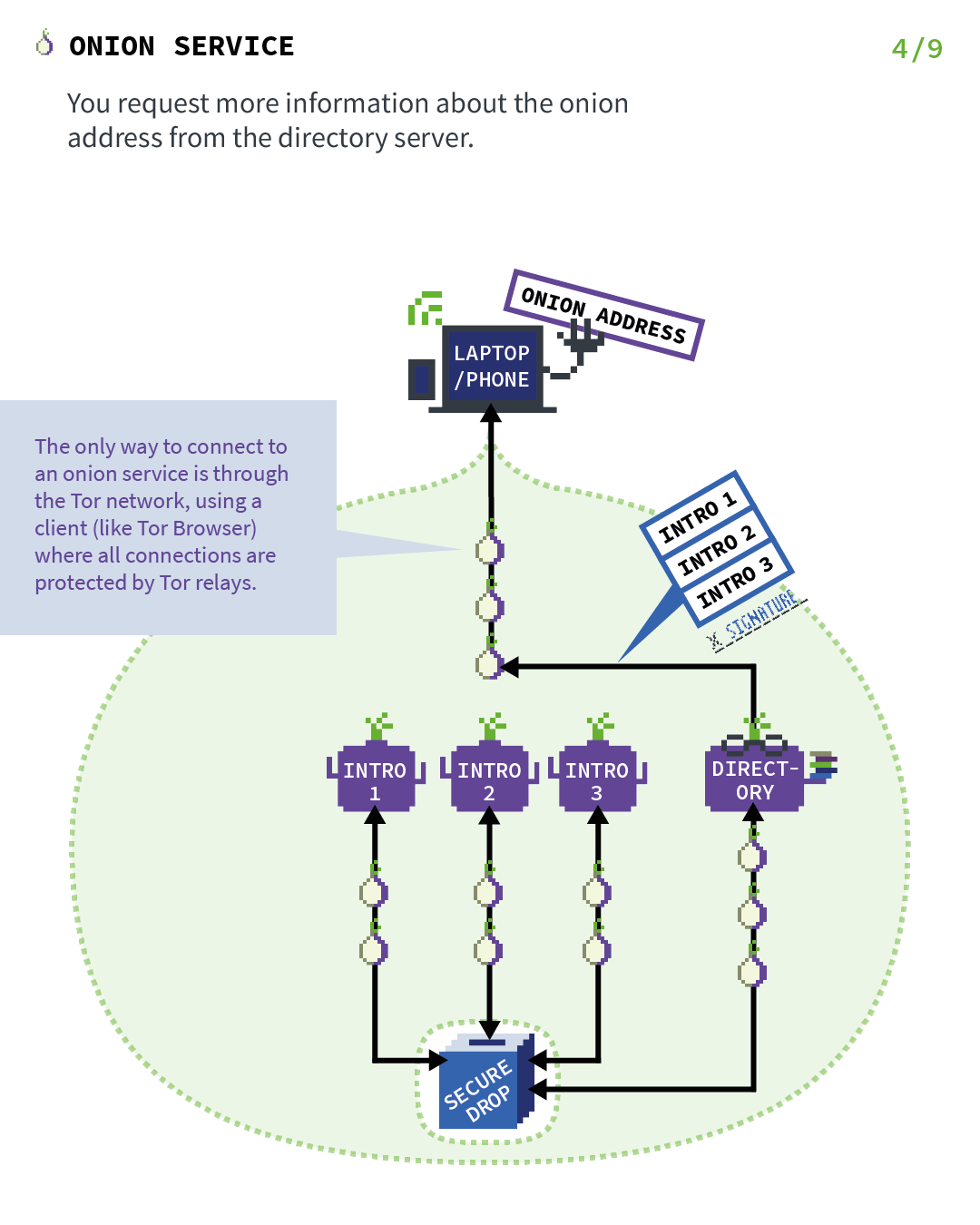
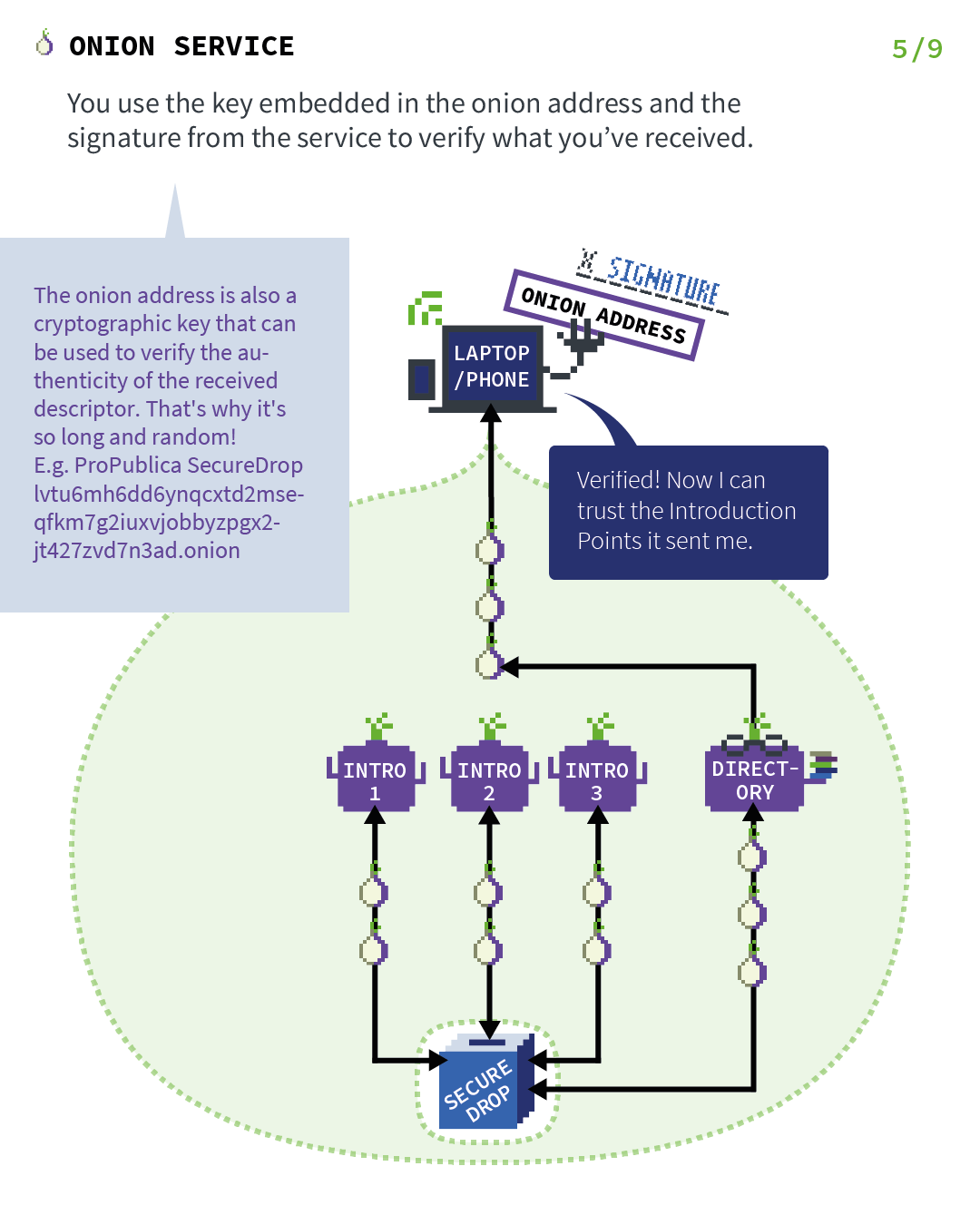
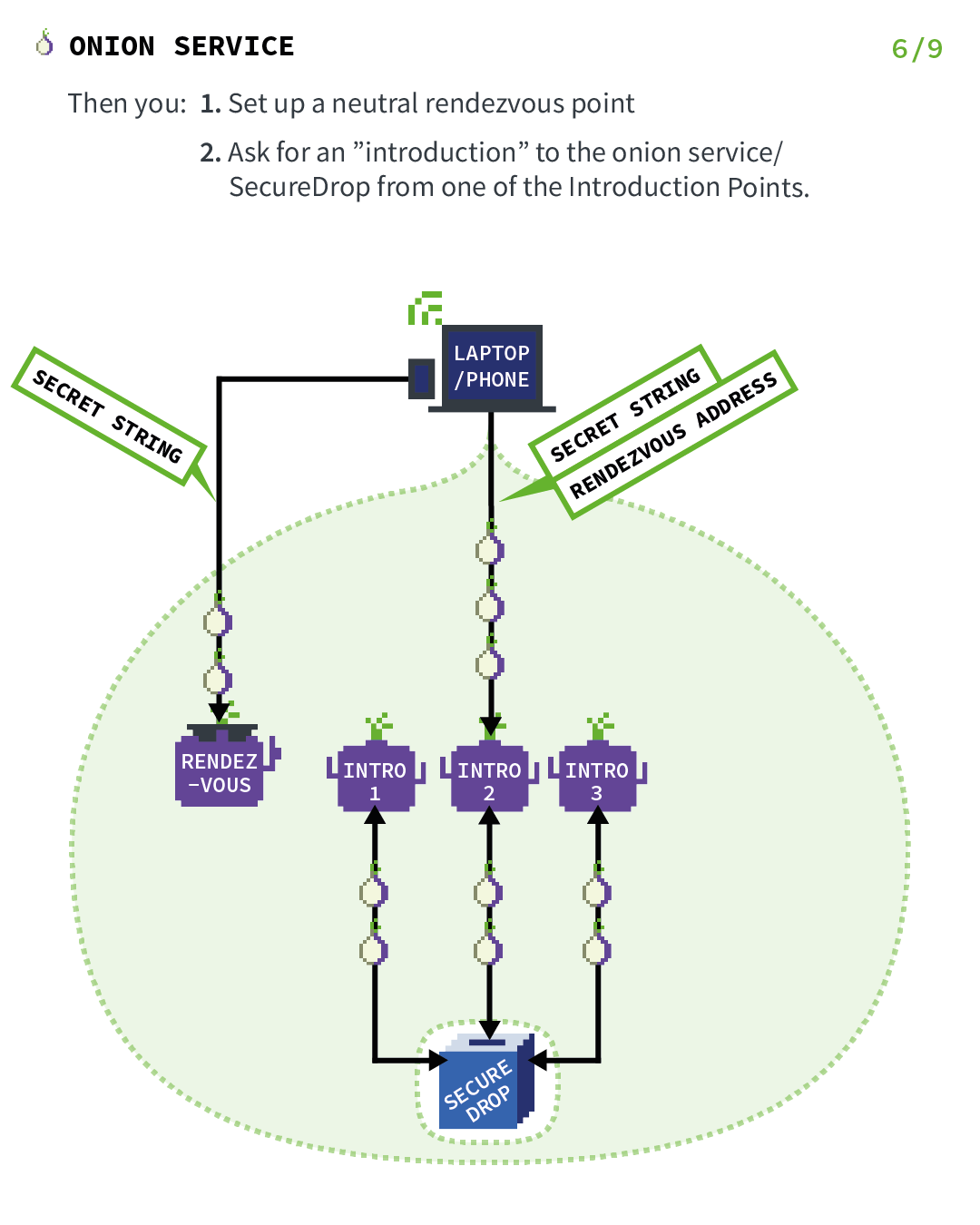
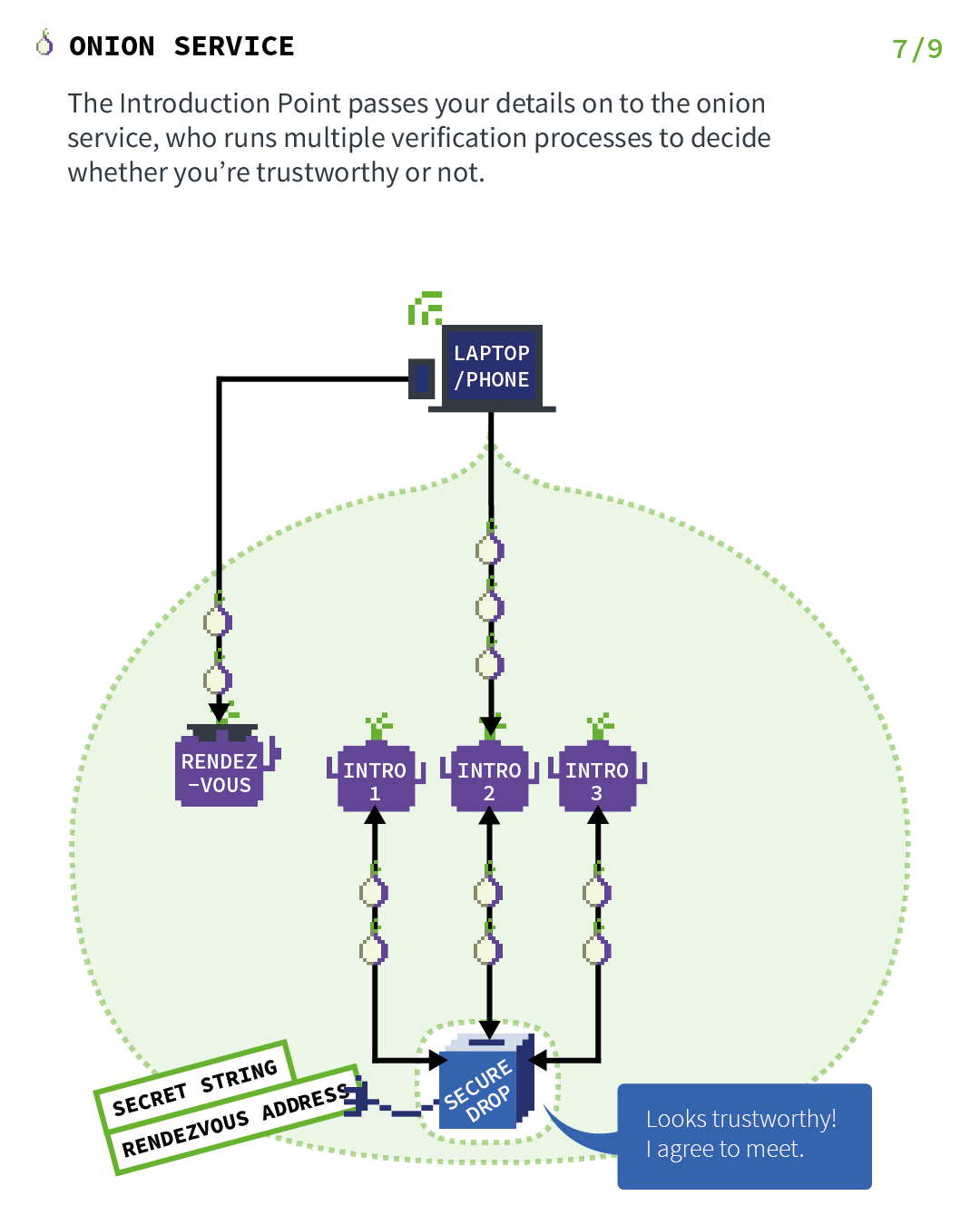
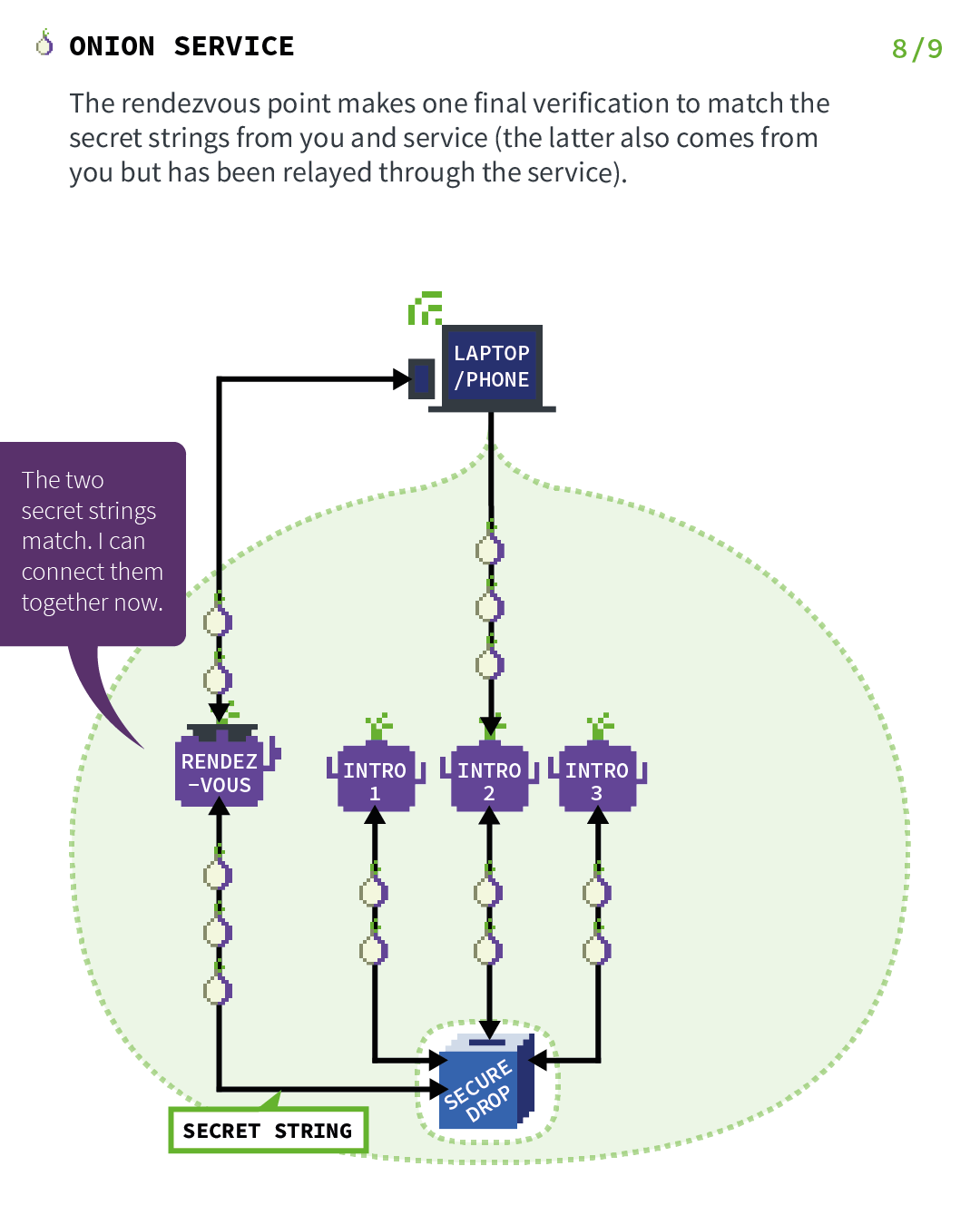
1.4. Getting back to Briar
So we were talking about Briar, or actually Bramble (Bramble reffers to the protocols while Briar reffers to the app, the implementation of those protocols). So let’s first divide it and see which protocols we have and treat them one by one.
- BQP (Bramble QR Code Protocol) for handling QR code (when you are near by and with physical access to the other device (i.e Bluetooth and LAN)
- BRP (Bramble Rendezvous Protocol) for handling briar:// links
- BHP (Bramble Handshake Protocol) for sharing keys (still with briar:// links)
- BSP (Bramble Syncronisation Protocol) for synchronising messages
- BTP (Bramble Transport Protocol) for actually transporting data (through Tor, Bluetooth or LAN)
1.4.1. How QR code works (BQP)
When contacts are near-by (can use bluetooth and/or LAN) then they should use QR codes to connect, it’s the safest method to connect on Bramble. And it uses the BQP (Bramble Qr Code Protocol)
- First both generate a key pair
- Then both generate a QR code containing a public key commitement (the first 16 bytes of the hash of the public key), the bluetooth MAC address and LAN IP address.
- They both scan each other’s QR code and try connect either by LAN, bluetooth or both.
- Once connection established, they both send their public key and compare them to the committement made.
- Diffie-Hellman is done with the keys and is hashed in order to generate a shared secret.
- A confirmation is sent containing a hash of the shared secret, the 2 public keyrs and the 2 QR code payloads. Those are exchanged, compared and must be identical.
- A new key is derived from the shared secret and the old keypair is deleted.
1.4.2. How briar:// links work (BRP and BHP)
Now there are 2 protocols for operating with briar:// links. The first one is called “Bramble Rendezvous Protocol” or BRP for short and is used to discover the peers in the network.
The second is called “Bramble Handshake Protocol” (or BHP) and is used to share keys and start chatting.
- BRP protocol
The briar:// link itself is a public key, even if it looks like it, it’s not the onion link itself, that way it cannot be used to track peers.
So when you add the other person’s public key and send your own public key to the other person. What happens is this:
- First, diffie-hellman is done with the public keys exchanged, so you both end up with a shared secret.
- Then some other stuff are done with it which ends up with a 64 caracter string, then two key pairs are made with the first half and the second half of the string (as seeds).
- Those key pairs are then used to create a TOR hidden service and thus get 2 onion links. One for you, and one for your friend!
- BHP protocol
The BHP is used to not use the same keys as for the contact discovery for actually sending messages. And creating a key pair that can be used for BTP.
- Both generate an ephemeral key pair
- They exchange their public keys
- They do a diffie-hellman and exchange a proof of ownership which proves the ownership of the sender’s long term public key and ephemeral public key and also binds to the recipient’s long term public key and ephemeral public key.
- Keys are deleted when communication’s over
1.4.3. TODO How messages are synchronized
1.4.4. Driving data through transports (BTP)
The goal of this protocol is to provide a way to flow data through the different transports (bluetooth, LAN, TOR, etc) with, among others,
- Flexibility. The protocol should be able to operate over a wide range of underlying transports with bandwidths varying from kilobits to gigabits per second, and with latencies varying from milliseconds to days.
- Concealability. The protocol shouldn’t reveal any information that could make the requests distinguishable from other protocols. If someone is listening to traffic, they shouldn’t be able to see that one is using Briar.
- Confidentiality. The adversary should not be able to learn what data is being carried by the protocol.
- Integrity. If the adversary truncates the data, the receiving peer should be able to detect that this has happened.
- Authenticity. The adversary should not be able to cause either peer to accept data from any third party as though it came from the other peer.
- Forward Secrecy. The adversary should not be able to learn what data was carried by the protocol if, at some later time, the adversary compromises one or both of the peer devices.
However, the protocol itself doesn’t grant anonymity, unlinkability or unobservability. If you want that you then should use TOR (see BRP and BHP above).
1.5. Sources and references
1.5.1. About Briar
Those are my sources about Briar itself. Those go from the most basic to the most advanced.
- How it works - Briar Project is a very simple overview of Briar’s security feature and stuff.
- Diving deep into Briar - a closer look at its internals at XMPP Meetup Berlin is a video explaining how Briar works. You can find the slides of the presentation here.
- Briar Wiki explains how each component and protocol works in much greater details.
1.5.2. Perfect forward secrecy and Diffie-Hellman
- Perfect Forward Secrecy in TLS Explained explains what is forward secrecy and how it works in practice in the example of TLS (forward secrecy is used to share keys in Briar)
1.5.3. How TOR Hidden Services work
Those are all the informations about TOR Hidden Services. They go from the basic components of it, to the full explanations.
- What are Distributed Hash Tables explains how DHT works (to understand hidden services)
- How TOR Works (Computerphile) explains how onion routing which is used for remote transport in Briar
- TOR Hidden Services (Computerphile) explains how hidden services work (requires understanding of onion routing and DHT understanding)
- How Does Tor Really Work? The Definitive Visual Guide (2020) Explains how tor and hidden services work in a non video format (requires understanding of DHT). Note: It seems part of this is inaccurate, but it does give a pretty good overview of TOR in general, beyond onion routing and hidden services.
- How do Onion Services Work is the official explanation from Tor Proect about hidden services (also called onion services) where all the images come from. It’s very easy to understand, but if you want a deeper understanding of it, I advise you to look at all the links above.